Regardless of company size, it is evident that people are under pressure to establish efficient security interfaces to sustain all sorts of breaches.
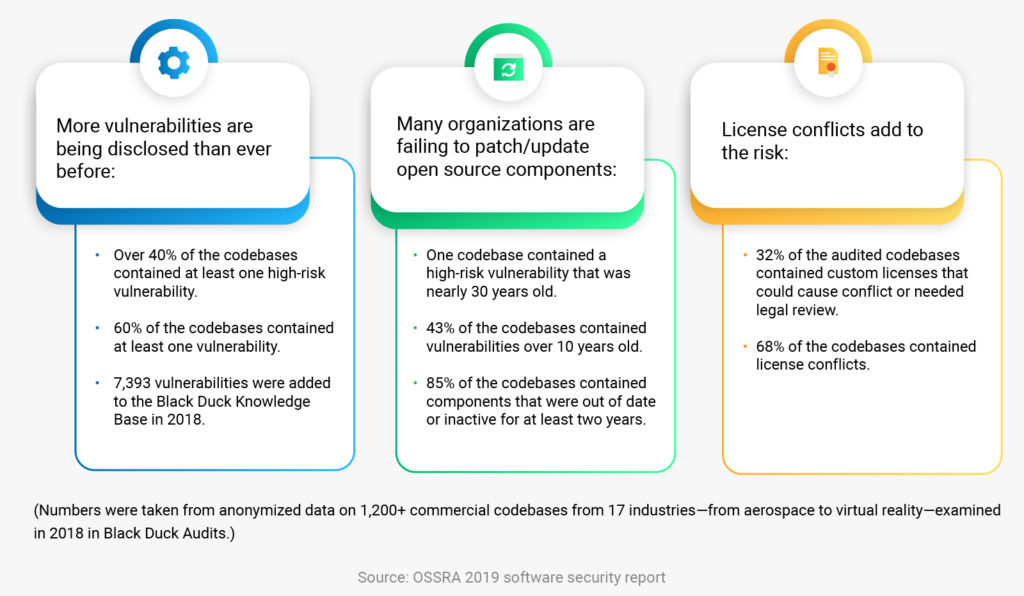
Odoo is one of the greatest foundations of open-source and modern software; if security concerns are not managed, it can bring code quality at risk. According to OSSRA’s 2019 software security report, over 40% of open-source codebases contained at least one high-risk vulnerability, and 60% of the codebases contained at least one vulnerability.
If we break down the OSSRA report, here’s why we may fear the security of the Odoo hosting server:
But there is always room for improvement. Knowing this, we at Aktiv Software have implemented various CIS (Center for Internet Security) checklists to ensure security for your Odoo hosting server.
Brief about CIS
CIS Benchmarks are developed through the generous volunteer efforts of subject matter experts, technology vendors, public and private community members, and the CIS Benchmark Development team.
The Center for Internet Security is a recognized industry standard for secure configuration guidance, developing comprehensive, consensus-derived checklists to help identify and mitigate known security vulnerabilities across a wide range of platforms.
Best Security Practices for Odoo Hosting Server
At Aktiv, we have created a mechanism that will automatically scan your server’s current configuration, find all loopholes, and finally fix them—doing all this in conjunction with the CIS Benchmarks.
However, we follow a rigorous CIS hardening procedure to eradicate vulnerabilities from your Odoo hosting server.
To name a few, here’s a list of checks we follow for you:
- Disable unused file systems
- Configure automatic software updates
- Secure Boot Settings
- Uninstall unnecessary and unwanted modules and/or processes
- Remove uncommon network protocols.
- Harden the server configuration via ‘sysctl’ file
- Configure ‘iptables’ with strict rule sets to block attacks
- Harden the ssh Server configuration
- Check User/Group settings
- Additional modules like SELinux, Fail2Ban, RKHunter
In case you want to know more about the server security hardening and its requirements at the Odoo deployment stage, you can contact our expert consultants.